
HOME | ABOUT US | INSIGHTS | WHITE PAPERS | CLIENT SERVICES | OUR ASSOCIATES | CONTACT US
Malware Landscape 2022 |
Insights | White Papers
Malware Landscape 2022:
A Study of the Scope and Distribution of Malware
Executive Summary Full Report
The study, which analyzed 2.5 million records of distinct malware events from April 1, 2021 to March 31, 2022 collected by the Cybercrime Information Center, explains what malware was most prevalent, where malware was served from, and what resources criminals used to pursue their attacks.
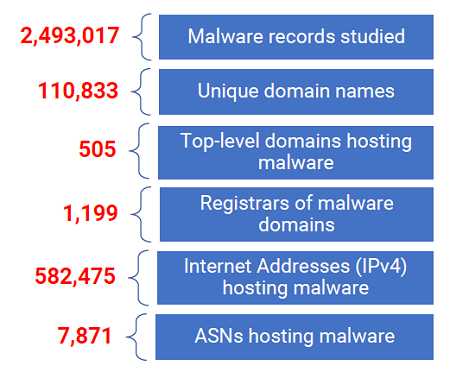
Among the major findings in the study, Interisle reports that:
- The most frequently reported malware targets Internet of Things devices - surveillance cameras, sensors, or embedded technologies.
- Asia-Pacific networks host most IoT malware. China, India, and Australia represent 81% of malware that targeted IoT devices.
- Information stealers, ransomware, and backdoors are the most prevalent "endpoint" malware, i.e., malicious software that targets tablets, mobile phones, laptops, and PCs.
- Networks in the United States and China host the most endpoint malware and 8 of the 10 registrars with the most malware domains reported are headquartered in North America.
- Domains registered in the new Top-level Domains (TLDs) are disproportionately attractive to malware attackers. The new TLDs represent only 8% of the domain name registration market, but they contained 24% of reported malware domains. By contrast, the country code TLDs represent 39% of the market, but only 26% of the reported malware domains.
- Malware attackers have made effective use cloud services, including file sharing services, code repositories, and storage services. While most uses of anonymous file sharing and code repositories are well-intentioned, malware attackers have used these services to distribute source code, attack code, and files containing compromised credentials or cryptographic keys.
You may read an Executive Summary of the Report or the complete Report.
Comments can be submitted to feedback@interisle.net
The opinions, findings, and conclusions or recommendations expressed in this report are the product of independent work conducted by Interisle Consulting Group, without direction or other influence from any outside party, including parties that may have provided funding to support the work.
World class expertise | |